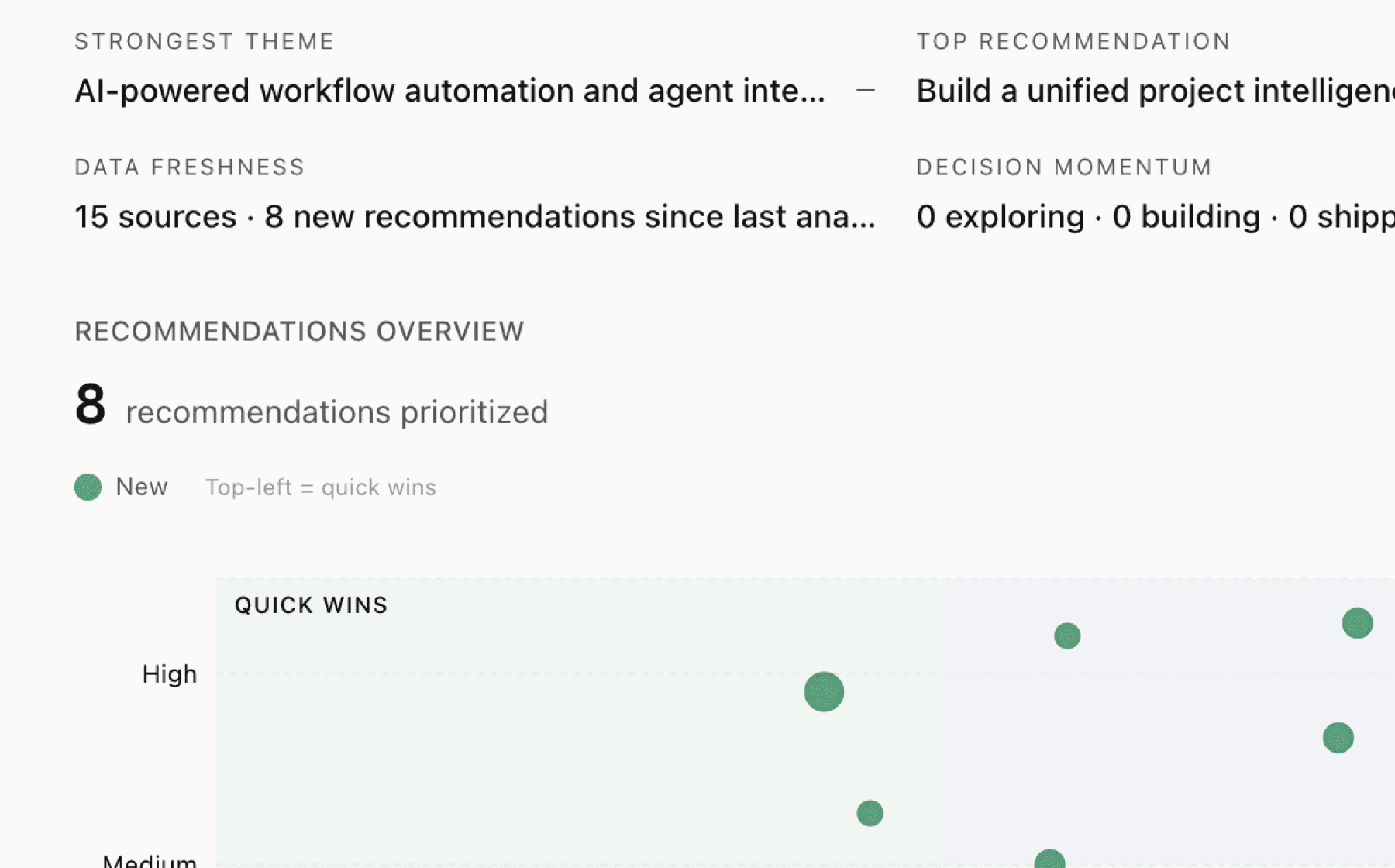
What Doppler users actually want
Mimir analyzed 14 public sources — app reviews, Reddit threads, forum posts — and surfaced 15 patterns with 8 actionable recommendations.
This is a preview. Mimir does this with your customer interviews, support tickets, and analytics in under 60 seconds.
Top recommendation
AI-generated, ranked by impact and evidence strength
Build comprehensive non-human identity lifecycle management with automated discovery, rotation, and decommissioning
High impact · Large effort
Rationale
Non-human identities now outnumber human identities in cloud-native environments but lack centralized oversight, creating critical security gaps. The Microsoft Azure Key Breach and AT&T Snowflake incident demonstrate how unrotated credentials enable extended attacker access. Organizations struggle with visibility into which NHIs exist, who owns them, and when they should expire.
The evidence shows manual rotation processes fail to scale, and static credentials persist far longer than necessary. Teams need automated discovery of all service accounts and API keys, continuous monitoring of their activity, automated rotation schedules, and automatic decommissioning of unused identities. This addresses the root cause of 49% of breaches involving compromised credentials.
Building this capability positions Doppler as the central control plane for the fastest-growing identity category in cloud infrastructure. As AI workloads multiply machine identities faster than teams can manually track them, this feature becomes table stakes for enterprise adoption and directly reduces breach risk while improving compliance posture.
Projected impact
The full product behind this analysis
Mimir doesn't just analyze — it's a complete product management workflow from feedback to shipped feature.
Evidence-backed insights
Every insight traces back to real customer signals. No hunches, no guesses.
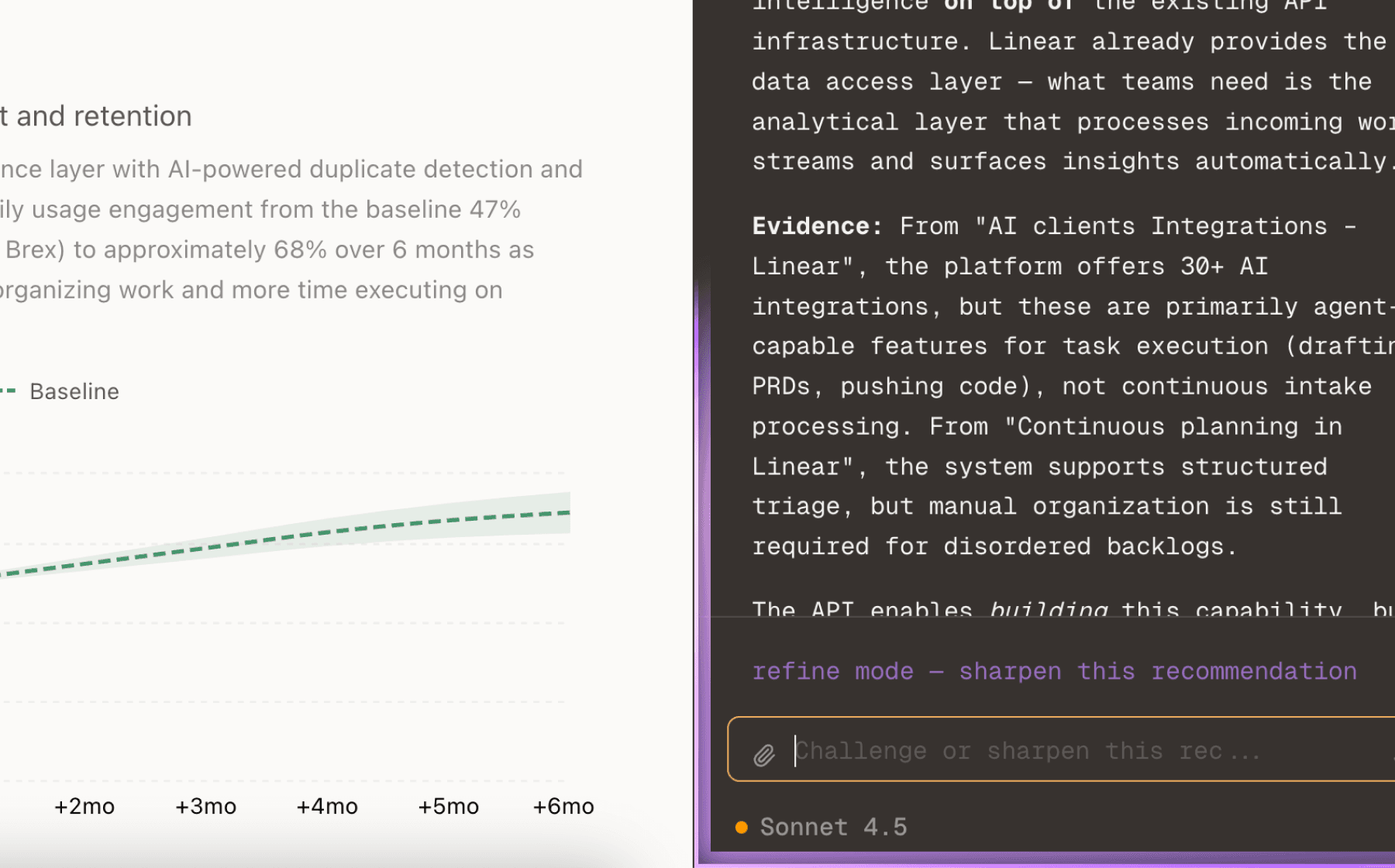
Chat with your data
Ask follow-up questions, refine recommendations, and capture business context through natural conversation.
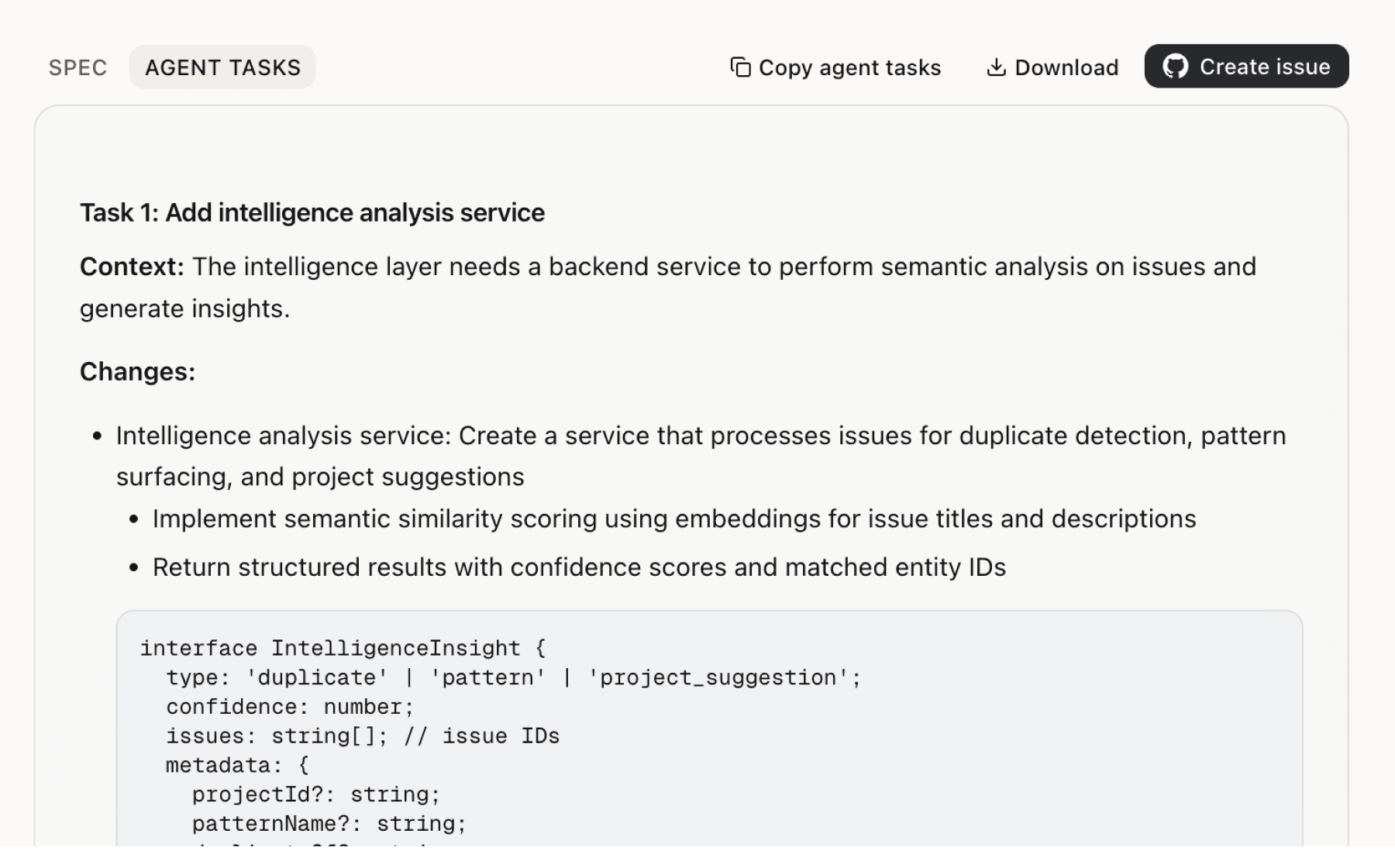
Specs your agents can ship
Go from insight to implementation spec to code-ready tasks in one click.
This analysis used public data only. Imagine what Mimir finds with your customer interviews and product analytics.
Try with your dataMore recommendations
7 additional recommendations generated from the same analysis
39 million secrets leaked on GitHub in 2024, and the EmeraldWhale attack exploited 110,000+ domains with exposed .env files to steal 15,000+ cloud credentials. Development environments have become the forgotten frontier of security, with secrets scattered across version control, local machines, CI/CD pipelines, and now LLM training data. Organizations lack visibility into where secrets exist and whether they're exposed.
Organizations need unified secrets management across AWS, Azure, GCP, Fly.io, and CI/CD tools without vendor lock-in or complex infrastructure. Current evidence shows Doppler already integrates with major platforms, but teams still struggle with setup complexity and maintaining consistency across fragmented vaults. The core insight is that secrets should move freely between cloud providers without manual intervention.
Beck's Hybrids achieved 5x faster developer onboarding and Retraced cut onboarding time by 80% with centralized secrets management. Current onboarding remains a multi-hour or multi-day process at most organizations, creating productivity loss and security risk as new developers either wait for access or receive overly broad permissions to speed things up. Teams report recovering 2 hours per developer per week through automation.
Compliance drifts because systems move faster than checklists, yet manual audit processes remain the norm. Organizations need compliance requirements expressed as enforceable policies that prevent violations rather than detect them after the fact. The current approach of comprehensive audit logs and detailed reporting is reactive, addressing compliance failures only during scheduled reviews rather than preventing them in daily workflows.
Secrets sprawl is inflating cloud bills with hidden costs that teams cannot measure or control. Current pricing shows no hidden fees and user-based models, but customers lack visibility into how secrets management impacts their overall infrastructure costs. One customer cut AWS costs by 10% with Doppler, suggesting significant optimization opportunities that most users don't discover.
AI workloads and agentic systems multiply machine identities faster than teams can manage them, creating new attack surfaces beyond traditional application secrets. LLM training exposes secrets during code review, AI copilots increase leakage risk, and distributed AI systems require managing model access tokens across multiple machines. The evidence from Ray and vLLM deployment shows teams need dedicated patterns for AI infrastructure secrets.
Teams consistently cite Vault as too complex with overly opinionated Kubernetes integration and cumbersome configuration requiring dedicated management teams. This represents a clear competitive opportunity, but migration friction prevents adoption. Organizations with existing Vault deployments face a binary choice between continuing with complexity or undertaking a risky migration project.
Insights
Themes and patterns synthesized from customer feedback
Doppler demonstrates strong traction with 47,000+ customers, 30+ billion monthly secrets reads, and customers reporting 200% ROI and successful enterprise deployments managing 1,300+ secrets at scale. Wide adoption across industries signals product-market fit and customer satisfaction.
“47,000+ startups and enterprises using Doppler”
Secrets management platforms require high uptime (99.95% SLO) and reliability to support mission-critical deployment workflows and maintain user trust in security-sensitive operations.
“Doppler maintains 99.99% historical annual uptime”
Platforms need webhooks, SDKs, and robust API support to enable automation, scale DevOps infrastructure, and maintain clean separation between secret management and business logic through dedicated secret retrieval functions.
“Platform includes webhooks and SDKs for API automation to support scaling DevOps infrastructure efficiently”
Secrets versioning with rollback support provides a safety net for configuration changes and enables faster remediation during security incidents without downtime.
“Doppler offers secrets versioning and rollback support as security features”
The majority of web application attacks stem from stolen credentials, establishing strong market need for robust secrets management solutions.
“86% of web application attacks stem from stolen credentials”
Teams need centralized platforms integrating seamlessly across AWS, Azure, GCP, Fly.io, and CI/CD tools to manage secrets across distributed DevOps workflows without requiring dedicated ops teams or complex infrastructure. Vendor neutrality and multi-cloud support prevent lock-in while simplifying management.
“Competing solutions like Vault are too complex, with overly opinionated Kubernetes integration, complex dynamic access, and cumbersome configuration requiring dedicated teams”
Secrets management overhead slows developer velocity and team onboarding; customers report 5x faster onboarding and significant weekly time recovery per developer with streamlined solutions. Easy integration, instant deployment, and minimal operational overhead are essential for adoption.
“Beck's Hybrids achieved 5x quicker developer onboarding with Doppler”
Teams need role-based access controls, approval workflows, automated audit logging with SIEM integration, and enterprise-grade features (AES-256-GCM encryption, SOC 2, ISO compliance) to meet compliance requirements without manual overhead and support scaling to thousands of services.
“Custom workflows to tailor secrets management to fit specific compliance needs”
Teams managing non-human identities at scale require transparent pricing without hidden fees and clear ROI messaging demonstrating efficiency gains. Freemium models with free Developer plans (3 users, no credit card) and low-cost Team plans ($21/user/month) lower barrier to entry for initial adoption.
“Team plan positioned as most popular with 14-day free trial and $21/mo per user pricing”
Traditional solutions like HashiCorp Vault are overly complex with opinionated configurations and fragmented multi-cloud architectures. Teams need simplified, modern tools with environment sync, drift detection, and local dev provisioning that eliminate the need for dedicated management teams.
“Competing solutions like Vault are too complex, with overly opinionated Kubernetes integration, complex dynamic access, and cumbersome configuration requiring dedicated teams”
Monitoring and alerts on secret access enable quick detection and response to irregular activities and potential breaches. Teams need dashboards and automation to maintain visibility across distributed secrets infrastructure.
“Doppler offers Git-style activity logs with rollback support, secrets referencing, and webhook notifications for secret changes”
Non-human identities (APIs, services, bots) now outnumber human identities but lack centralized oversight, clear ownership, and automated lifecycle management. Organizations need visibility into which NHIs exist, their permissions, automated credential rotation, continuous monitoring, and decommissioning to prevent extended attacker access from compromised service accounts.
“NHIs now outnumber human identities in most cloud-native environments”
Secrets leak across development environments, version control, .env files, LLM training, and unmanaged infrastructure, enabling attacks like EmeraldWhale that steal thousands of credentials. Centralized management with real-time visibility is required to prevent exposure and reduce hidden costs.
“Development environments have become forgotten frontier of organizational security”
49% of breaches involve compromised credentials. Organizations need comprehensive audit logs, detailed reporting, automated secrets rotation, continuous monitoring, and compliance-as-code to meet regulatory requirements (HIPAA, SOC 2) and detect unauthorized access. Audit trails must be continuous and automated as systems evolve.
“49% of breaches involve compromised credentials”
Static, long-lived credentials create persistent security risks; teams need ephemeral tokens, automatic expiration, frequent rotation, and closed-loop lifecycle management with detection, propagation, and verification across complex environments. Current manual processes fail to scale in fast-moving development environments.
“Manual secrets management processes like credential rotation and environment sync fall apart in fast-moving development environments and don't scale.”
Run this analysis on your own data
Upload feedback, interviews, or metrics. Get results like these in under 60 seconds.