What Multifactor users actually want
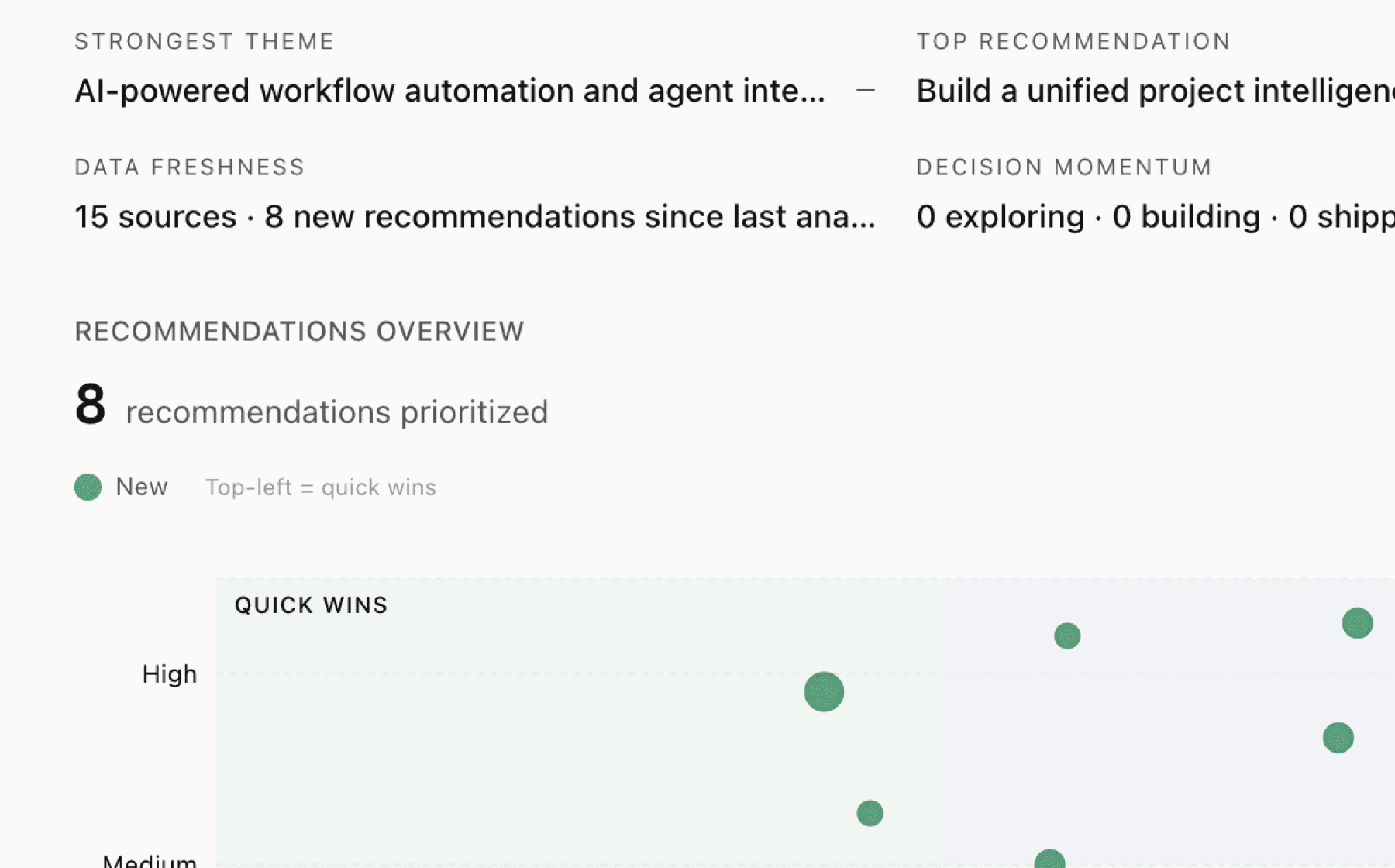
Mimir analyzed 15 public sources — app reviews, Reddit threads, forum posts — and surfaced 15 patterns with 8 actionable recommendations.
This is a preview. Mimir does this with your customer interviews, support tickets, and analytics in under 60 seconds.
Top recommendation
AI-generated, ranked by impact and evidence strength
Build a self-serve AI agent onboarding flow that demonstrates instant revocation in under 60 seconds
High impact · Medium effort
Rationale
The data shows critical market timing: enterprises are deploying agentic applications faster than security measures can keep up, and Multifactor has built the technical foundation (Checkpoint, Switchboard, cryptographic AAA) to solve the zero-trust problem for AI agents. However, the research reveals no evidence of user-facing onboarding or activation experiences that translate this sophisticated technology into immediate value for product managers and engineering leads.
A focused onboarding flow that lets users connect an AI agent, grant specific permissions, watch it perform an action, and then instantly revoke access would demonstrate the core value proposition in the first minute. This directly addresses the primary metric of user engagement and retention by creating an aha moment before users encounter friction. The flow should emphasize what's impossible with traditional password managers—true revocability, non-repudiable audit logs, and granular permissions—using plain language that resonates with the target audience.
This recommendation synthesizes the technical capabilities across themes (instant revocation, fine-grained permissions, AI-specific architecture) into a single activation experience that converts research credibility into product adoption.
Projected impact
The full product behind this analysis
Mimir doesn't just analyze — it's a complete product management workflow from feedback to shipped feature.
Evidence-backed insights
Every insight traces back to real customer signals. No hunches, no guesses.
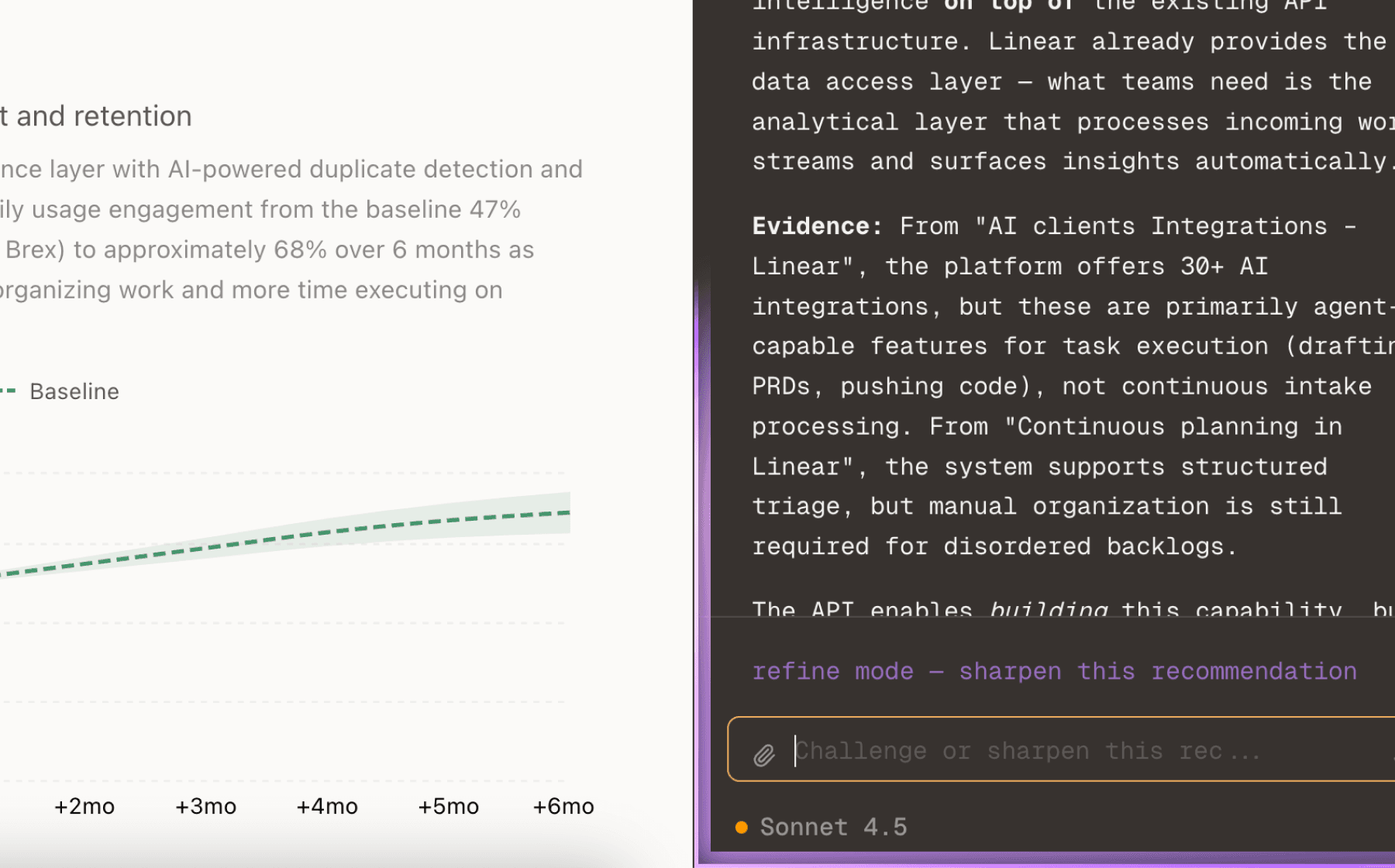
Chat with your data
Ask follow-up questions, refine recommendations, and capture business context through natural conversation.
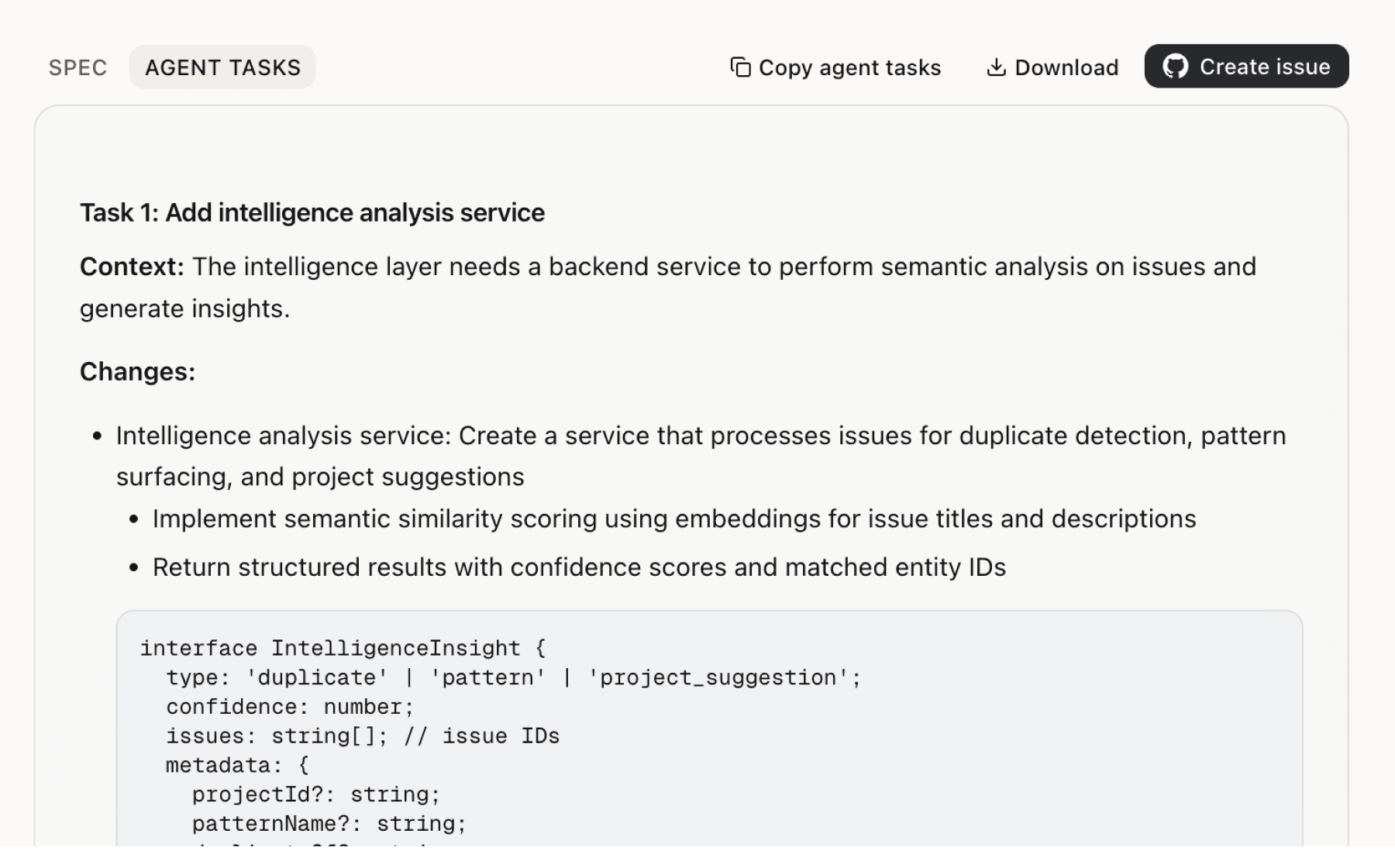
Specs your agents can ship
Go from insight to implementation spec to code-ready tasks in one click.
This analysis used public data only. Imagine what Mimir finds with your customer interviews and product analytics.
Try with your dataMore recommendations
7 additional recommendations generated from the same analysis
The research shows Multifactor has deep technical credentials (USENIX Security publications, CIA/NASA backgrounds, Zcash grants) and explicitly targets AI Safety as a dedicated solution, but there's no evidence of packaged implementation guidance for specific buyer personas. Product managers and engineering leads evaluating zero-trust solutions need to see how the platform maps to their compliance requirements and security workflows before committing.
The research includes strong positioning claims that password managers are broken and Multifactor changed the game, but there's no evidence of structured competitive differentiation that helps buyers understand the architectural differences. Users need to understand why instant revocation, non-repudiation, and fine-grained permissions are impossible with shared encryption keys before they'll invest time evaluating a new category.
The research shows comprehensive audit capabilities and non-repudiable logging as core technical strengths, but there's no evidence these capabilities are surfaced in real-time monitoring interfaces that help users maintain operational control over AI agents. Product managers and engineering leads deploying agentic applications need continuous visibility into agent behavior to catch security issues before they escalate.
The research shows MFKDF2 won a Distinguished Artifact Award at USENIX Security and is fully backward compatible with existing authentication factors, but there's no evidence of developer-facing distribution that makes it easy for engineering teams to integrate the technology. The research also shows the company frequently licenses software under BSD to promote innovation, indicating openness to broader adoption strategies.
The research shows Multifactor emphasizes research credibility, transparent governance with stakeholders, and ethical security issue management, but there's no evidence of public transparency mechanisms that build trust with security-conscious buyers. Engineering leads evaluating zero-trust infrastructure need to see how the platform performs under stress and how the company responds to security issues.
The research shows Checkpoint enables secure sharing with AI agents via computer use and browser use platforms, but there's no evidence of ecosystem partnerships that make Multifactor the default security layer for agentic applications. The stated mission is to redefine zero-trust for the agentic web, but achieving category leadership requires distribution through the platforms where AI agents are being built.
The research identifies compliance with complex regulations as a core use case and highlights that cloud environments struggle with juggling multiple compliance requirements. However, there's no evidence of packaged compliance solutions that reduce the evaluation burden for regulated industries like financial services, healthcare, or government contractors.
Insights
Themes and patterns synthesized from customer feedback
Multifactor collects personal and non-personal data with vendor restrictions, uses cookies for behavior tracking, and reserves rights to share information with legal/governmental requests. The company has no obligation to backup user content, establishing clear boundaries of user responsibility.
“Terms of Use document for Multifactor authentication product; includes mandatory arbitration clause with 30-day opt-out period and class action waiver”
Multifactor enforces strict trademark usage rules preventing incorporation into third-party product names and requiring formal partnership agreements for service resale. This protects brand integrity, prevents IP infringement through phishing or misuse, and ensures authorized distribution.
“Word marks (not logos) can be used to identify Multifactor products/services; logo use requires prior written permission”
Playbooks feature enables reusable automations combining natural language with pre-configured permissions, supporting complex organizational structures and time-varying access levels across teams and folders without requiring manual reconfiguration.
“Playbooks feature enables reusable automations combining natural language commands with pre-configured permissions for complex task automation.”
Terms of service reserve right to modify or discontinue service without notice, provide no warranty guarantees, and explicitly disclaim liability for breaches despite security protections. Users must indemnify Multifactor for claims arising from their use or policy violations.
“Company reserves right to modify, suspend, or discontinue the Site without notice and has no obligation to provide support or maintenance”
Multifactor offers browser extensions with autofill, autosave, and passkeys capabilities across major platforms (Chrome, Mac, Microsoft, iOS, Android) plus extensive support infrastructure including documentation, portal, blog, videos, and status page, enabling seamless adoption.
“Company provides extensive support infrastructure including documentation, support portal, blog, videos, and status page for transparency”
Solution positions across AI Safety, Healthcare, Web3, Finance, and AR/VR industries with specialized focus on zero-trust authentication for modern web threats including post-quantum security, demonstrating broad market relevance.
“Product offers specialized solutions across multiple high-value industries including AI Safety, Healthcare, Web3, Finance, and AR/VR”
Strong market validation evidenced by Y Combinator backing (F25 batch), $15M seed funding, and additional backing from Pioneer Fund, NSF, and Berkeley Center for Responsible Decentralized Intelligence, positioning the company as credible player in zero-trust security.
“Company is Y Combinator backed (F25 batch) with additional backing from Pioneer Fund, NSF, Berkeley Center for Responsible Decentralized Intelligence, and others.”
Multifactor's research team has produced dozens of patents, publications, and open-source projects advancing zero-trust security, with strong academic credentials and research featured in top venues (USENIX Security, PETS) and recognized with grants. The proprietary technology stack includes MFKDF2, Switchboard, and Checkpoint platforms forming the core of its zero-trust infrastructure.
“Company emphasizes research credibility with publications in USENIX Security, PETS, IEEE EuroS&P, ACM UIST, and ACM CHI venues.”
Identity is the root cause of cloud security breaches and the first/last line of defense. Multifactor binds identity to multiple authentication methods (biometrics, hardware tokens) and achieves user indistinguishability—making apps harder to attack while users notice no change—using cryptographically-backed guarantees.
“Cloud-native authentication solution that binds data to multiple authentication methods including biometrics and hardware tokens”
Multifactor enforces patents on core technologies while explicitly allowing use by academic researchers and non-profits, and frequently licenses software under open-source licenses (BSD) to promote innovation. This strategy gives confidence to invest in long-term research while protecting IP through patents that require separate licensing.
“Multifactor frequently licenses software under open source licenses to promote innovation and collaboration”
Zero-trust implementation requires comprehensive, traceable audit capabilities to track all access and actions with non-repudiable proof of who accessed accounts and what actions they performed. This contrasts with existing solutions that offer no visibility into account usage and is essential for compliance and security investigation.
“"Multifactor redefines zero-trust account management with fine-grained sharing, detailed audit trails, and a world-class security architecture."”
Multifactor is a registered Delaware Public Benefit Corporation with a mission to enhance cybersecurity and privacy embedded in the corporate charter. The company offers free or discounted services to at-risk individuals and organizations including journalists, human rights defenders, and NGOs, viewing patents as innovation protection aligned with public benefit rather than competition-stifling.
“Company mission is to reinvent zero trust for the modern web, embedded in corporate charter and used as evaluation lens for all business decisions”
Current password managers lack granular control and true revocability—once shared, credentials can be copied and redistributed. Multifactor's Checkpoint technology enables secure one-click sharing and instant revocation of account access without password rotation, solving a critical pain point for team and AI agent collaboration.
“Password managers scatter credentials, lack granular sharing controls, and provide untraceable access—creating security gaps for team collaboration.”
Multifactor's core mission is building trustless authentication, authorization, and auditing infrastructure specifically designed for AI agents operating on the agentic web. The platform uses cryptographic guarantees to enforce security without requiring trust in intermediaries, addressing the emerging threat landscape where AI agents act faster than humans and probe for security flaws at scale.
“Multifactor enables trustless enforcement across authentication, authorization, and auditing using cryptographic guarantees”
Traditional shared encryption keys create impossible revocation scenarios and lack access granularity. Switchboard uses Proxy Re-Encryption to decouple data from access rights, enabling granular permissions (including write-only access) with true revocability while simultaneously achieving security, efficiency, and flexibility.
“Shared encryption keys create no granularity in access control and enable impossible revocation—users retain keys and can still decrypt data”
Run this analysis on your own data
Upload feedback, interviews, or metrics. Get results like these in under 60 seconds.