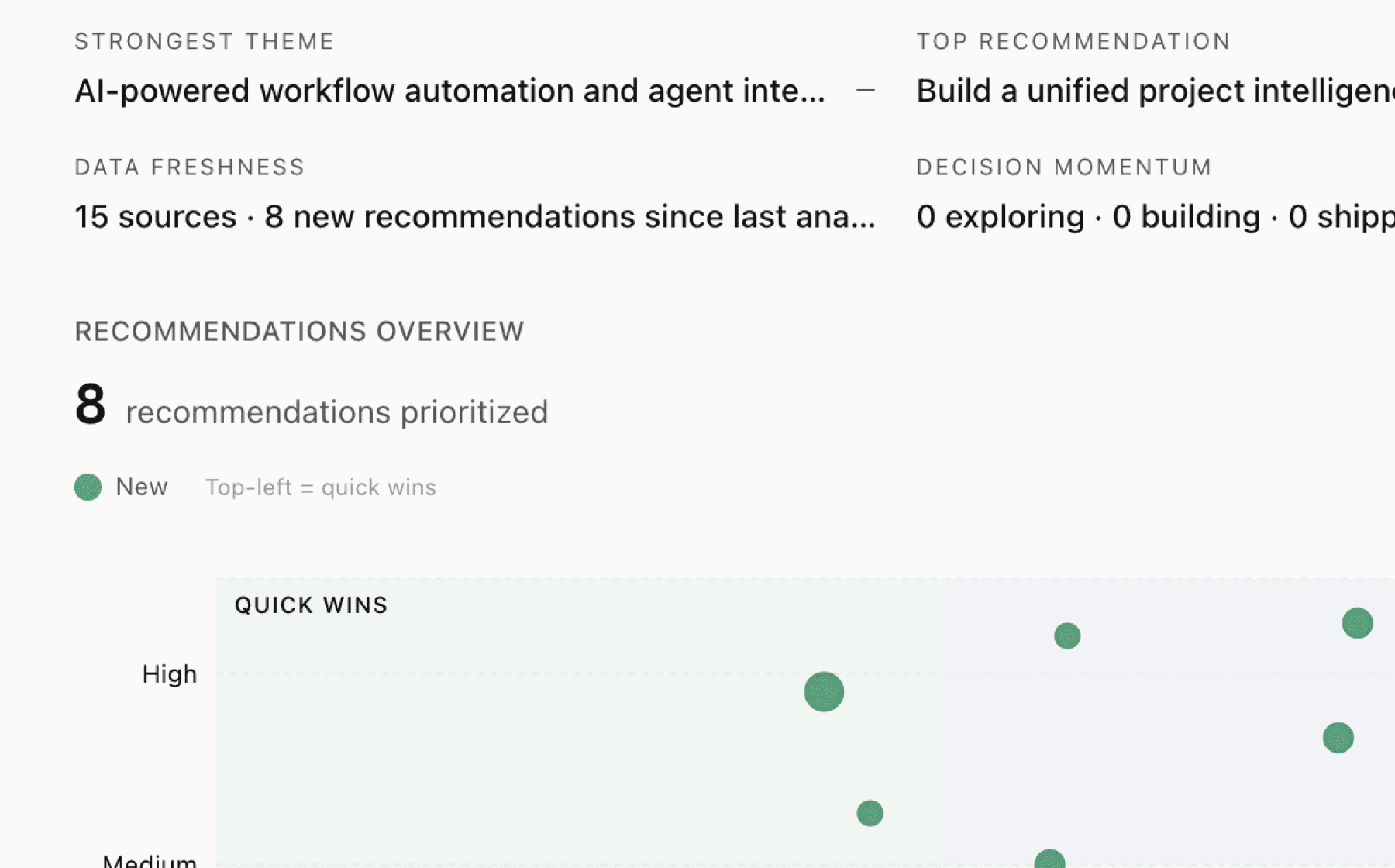
What Pangolin users actually want
Mimir analyzed 15 public sources — app reviews, Reddit threads, forum posts — and surfaced 15 patterns with 8 actionable recommendations.
This is a preview. Mimir does this with your customer interviews, support tickets, and analytics in under 60 seconds.
Top recommendation
AI-generated, ranked by impact and evidence strength
Build enterprise-grade compliance and audit tooling to accelerate upmarket expansion
High impact · Large effort
Rationale
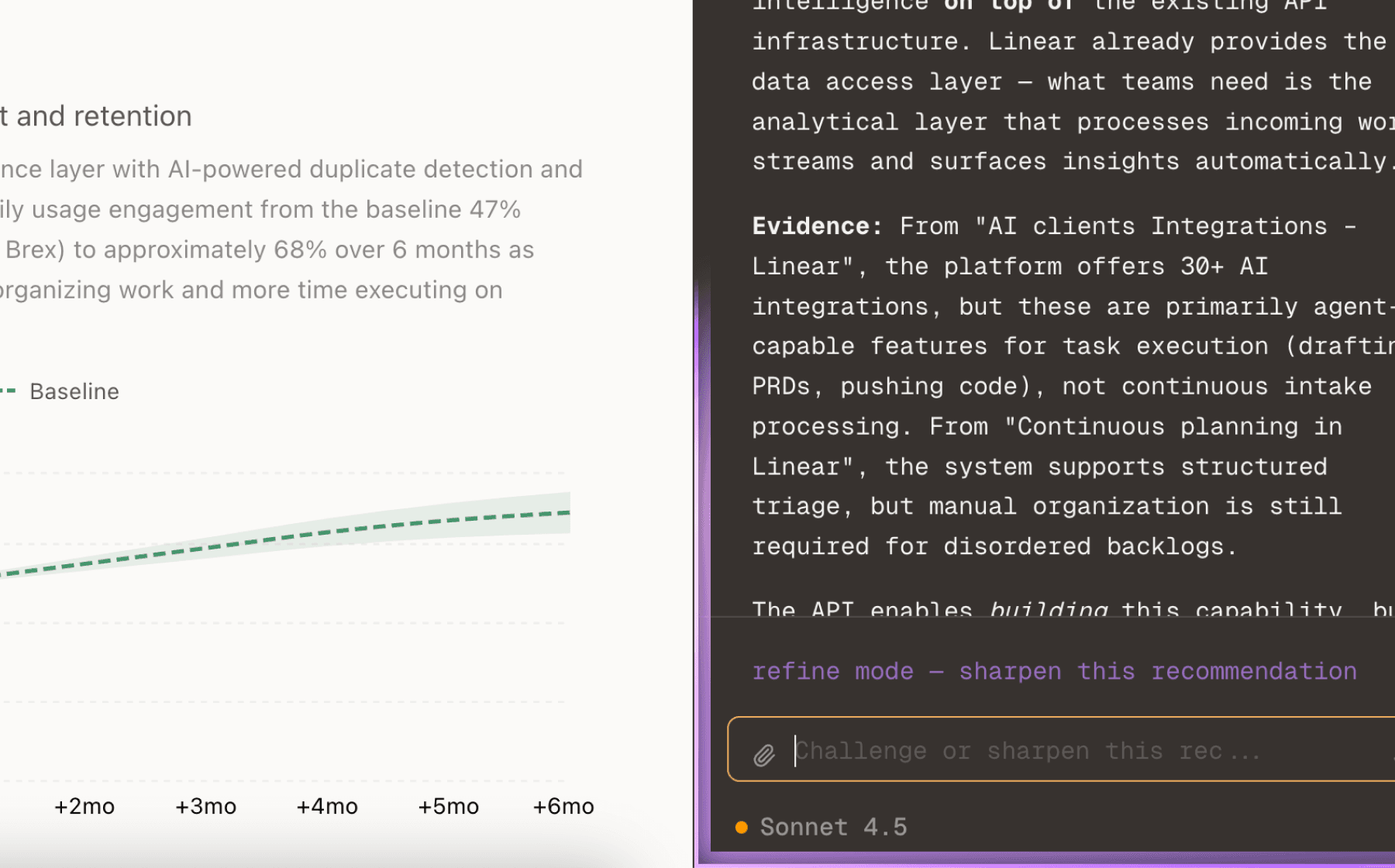
The freemium model successfully drives acquisition (1.1M+ deployments, 18.8K GitHub stars), but monetization remains concentrated at lower tiers. Advanced compliance features like log push, credential rotation, and extended retention are already gated to Business/Enterprise tiers, yet Enterprise Edition features remain unavailable. This gap blocks revenue from security-conscious buyers who represent the highest willingness-to-pay segment.
The seed funding provides runway to accelerate development, and the company explicitly needs sustainable monetization beyond the open-source core. Compliance tooling directly supports this goal by creating clear enterprise value that justifies premium pricing without undermining the community edition.
Prioritize audit log export APIs, SIEM integrations, compliance reporting templates (SOC 2, ISO 27001), and automated credential rotation workflows. These features align with the zero-trust architecture positioning and unlock revenue from regulated industries requiring data sovereignty and full audit trails.
Projected impact
The full product behind this analysis
Mimir doesn't just analyze — it's a complete product management workflow from feedback to shipped feature.
Evidence-backed insights
Every insight traces back to real customer signals. No hunches, no guesses.
Chat with your data
Ask follow-up questions, refine recommendations, and capture business context through natural conversation.
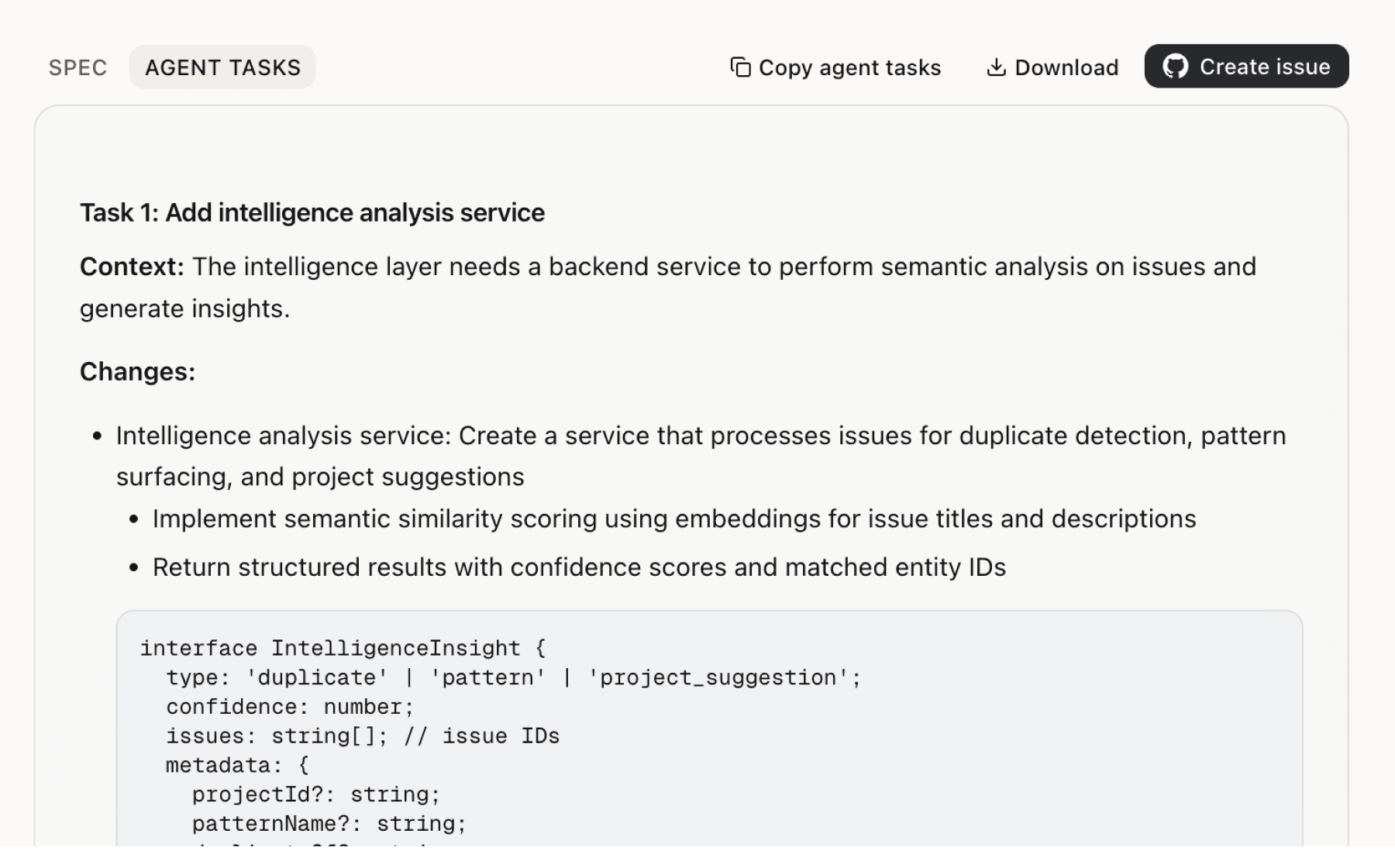
Specs your agents can ship
Go from insight to implementation spec to code-ready tasks in one click.
This analysis used public data only. Imagine what Mimir finds with your customer interviews and product analytics.
Try with your dataMore recommendations
7 additional recommendations generated from the same analysis
Pangolin competes on self-hostability and data sovereignty against cloud-only alternatives like Twingate and Tailscale, yet the path from open-source curiosity to paid enterprise deployment remains unclear. The company actively publishes competitive comparisons and positions hybrid deployment as a key differentiator, but lacks a structured onboarding flow that demonstrates this value quickly.
Pangolin Blueprints enable declarative configuration via YAML and Docker labels, but adoption requires understanding the abstraction model and building configuration from scratch. Infrastructure teams managing temporary environments, multi-site deployments, and hybrid cloud setups need proven reference architectures they can adapt quickly.
iOS and Android apps launched recently, expanding market reach to mobile-first organizations and BYOD workflows, but the onboarding experience likely mirrors desktop patterns rather than mobile-native behaviors. Contractors and remote workers using personal devices face higher friction than employees with corporate-managed endpoints.
The freemium model drives strong acquisition with 1.1M+ deployments and nearly 1,000 individual donors, yet conversion mechanics from free to paid tiers remain unspecified. The pricing structure creates a growth chasm: teams outgrow the 5-user Basic tier but face sticker shock jumping to Team tier with per-user pricing and minimum commitments.
Pangolin demonstrates strong performance with 156-245 Mbps download throughput depending on connector type, yet these metrics appear only in marketing materials rather than live product telemetry. Buyers evaluating alternatives need confidence that performance claims hold in their specific network topology and geographic distribution.
Enterprise Edition offers generous free usage for businesses under $100K annual revenue but requires paid licenses for larger businesses, yet procurement mechanics remain unclear. The support plan structure includes minimum user commitments and 12-month terms, suggesting manual sales processes that introduce friction for mid-market buyers comfortable with self-service purchasing.
Pangolin differentiates on architecture decisions like hub-and-spoke versus mesh, connector-per-network versus device-centric models, and resource-centric versus network-centric access control. These choices directly impact scalability, cognitive load, and operational complexity, yet the reasoning remains scattered across competitive comparison blog posts.
Insights
Themes and patterns synthesized from customer feedback
Pangolin offers tiered support plans (Basic, Professional, Enterprise) with escalating response SLAs, 15-minute scheduled calls with engineers, and multiple support channels (email, Slack, Discord, phone) to reduce friction and strengthen customer relationships. Support accessibility and engagement programs scale with customer tier and technical sophistication.
“Three tiered support plan structure (Basic, Professional, Enterprise) with increasing response SLAs and pricing”
Pangolin demonstrates strong throughput performance (156–245 Mbps download, 67–203 Mbps upload depending on connector type) and uses a scalable client-to-site-to-resource data path that avoids routing private traffic through central servers. Health checks, load balancing, and multi-subnet support (with overlapping CIDR handling) address operational reliability needs for production environments.
“Edge device site connector demonstrates 89.0 Mbps download and 67.0 Mbps upload throughput.”
Pangolin tracks acquisition across diverse channels (Search Engine, Social Media, Word of Mouth, GitHub, Blog/Article, Conference/Event) and has built 3,600+ Discord community members through organic channels like YouTube, podcasts, and articles. This comprehensive go-to-market approach demonstrates product-community fit and sustained expansion within developer communities.
“Primary customer acquisition sources tracked: Search Engine, Social Media, Word of Mouth, GitHub, Blog/Article, Conference/Event.”
Pangolin provides real-time access logging with detailed decision reasoning (granted, denied, blocked) and scales log retention with tier (3 days to 90 days to custom), supporting audit trails and compliance requirements. Device lifecycle management via archiving (rather than deletion) preserves audit history while keeping the UI clean.
“Archiving (not deletion) preserves audit trail while keeping UI clean; blocking devices immediately kills access”
Pangolin uses a freemium model with a free Basic tier (5 users) and scaling user limits across tiers (Home $12.50/month, Team, Business) to enable low-friction acquisition and gradual monetization. Advanced features like compliance tools, branding, and API access are gated to higher tiers, aligning monetization with customer willingness-to-pay and technical sophistication.
“Pangolin offers a freemium model with Basic tier supporting up to 5 users at no cost, enabling low-friction user acquisition.”
Pangolin provides identity-aware reverse proxy with clientless browser access for web applications via custom domains and automatic SSL, alongside native iOS and Android apps for zero-trust network access across all platforms. This eliminates installation friction for contractors, BYOD workflows, and expands addressable market to mobile-first organizations.
“Pangolin offers clientless browser access to web apps via identity-aware reverse proxy with custom domains and automatic SSL; Twingate requires client for all private resource access.”
Pangolin's hub-and-spoke, connector-per-network model scales more efficiently than mesh architectures (Tailscale) or device-centric alternatives (NetBird) for large deployments, while hiding the underlying network topology and showing users only authorized resources. This reduces cognitive load and security surface area compared to overlay IP management approaches.
“Pangolin uses flat site model for scaling (better for IoT/hundreds of sites); Twingate uses logical networks grouping for connector organization.”
Pangolin Blueprints enable declarative, YAML-based resource and policy definitions via Docker labels, automating service discovery and access control across temporary environments, multi-site deployments, and hybrid multi-cloud setups. This reduces configuration drift, improves team collaboration on network policies, and supports infrastructure teams managing diverse environments.
“Infrastructure-as-Code support via Pangolin Blueprints with YAML and Docker Labels, enabling programmatic proxy configuration.”
Pangolin offers flexible deployment models including self-hosted, cloud SaaS, and hybrid architectures with self-hosted traffic nodes, giving organizations full control over the data plane and compliance posture. This positions the product for regulated industries and data-sovereignty-conscious buyers who require control without vendor lock-in.
“Pangolin supports self-hosting full stack or hybrid cloud with optional self-hosted nodes; Tailscale is cloud-only managed service with Headscale as unsupported community option”
Pangolin uniquely supports public ingress tunnels (like Cloudflare Tunnel and ngrok) with load balancing and clientless web app access via identity-aware reverse proxy—features competitors like Twingate and NetBird lack. This enables frictionless developer experience for exposing development servers and internal tools through secure tunnels without signup friction.
“Pangolin supports public ingress tunnels (like Cloudflare Tunnel/ngrok) with load balancing and failover; Twingate focused on private resource access only.”
Pangolin employs a demo-first approach allowing immediate tunnel creation without account setup, combined with emphasis on ease of use and speed to support user engagement and reduce barriers to trial conversion. The product removes friction from initial evaluation, though long-term tunnel management requires account creation.
“Demo-first approach allows users to experience tunnel creation immediately without account creation”
Pangolin provides a centralized management interface for multiple application types (Bitwarden, Grafana, APIs, microservices) across distributed systems, reducing operational complexity for administrators managing diverse infrastructure. This consolidation simplifies access control and auditing across heterogeneous environments.
“Platform includes unified dashboard for managing applications across multiple systems (Bitwarden, Grafana, APIs, microservices, etc.).”
Pangolin differentiates through AGPLv3 open-source code, self-hostability, and full transparency while balancing sustainable business via a freemium model with separate Community and Enterprise editions. This approach maintains community trust through ethical monetization that does not force early adoption costs on small users or open-source advocates.
“Pangolin is an open-source, identity-based remote access platform built on WireGuard enabling secure connectivity to private and public resources.”
Pangolin implements identity-based, resource-centric remote access with granular controls including IP blocking, geoblocking, device approvals, device posture checks, and role-based policies that define specific applications rather than entire networks. This architecture differentiates the product from device-centric and mesh-based competitors by reducing cognitive load and security surface area.
“Pangolin provides granular, context-aware access control with IP blocking, geoblocking, and permission-based enforcement.”
Pangolin achieved 1.1M+ deployments, 18.8K+ GitHub stars, nearly 1,000 individual donors, and closed a $4.7M seed round in August 2025, demonstrating strong product-market fit and organic peer-to-peer adoption within developer communities. The product matured from beta to production stability in one year with consistent monthly active usage.
“Pangolin has achieved 1.1M+ deployments across Docker Hub and other platforms.”
Run this analysis on your own data
Upload feedback, interviews, or metrics. Get results like these in under 60 seconds.